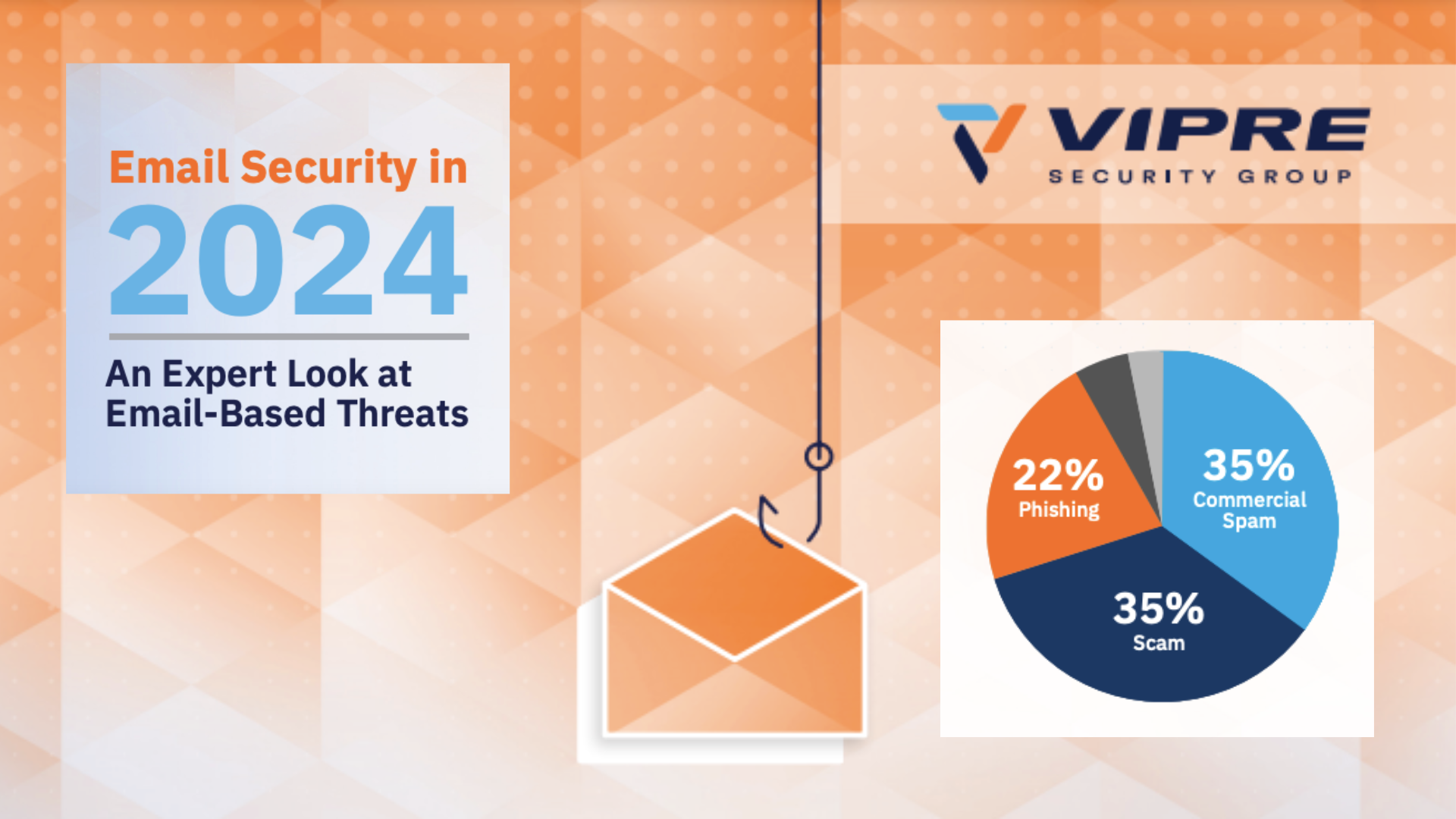
Cyber criminals stole more than $28 billion through email fraud from 2016-2020, according to FBI; new Chubb paper urges companies to reevaluate their business procedures and invest in updated technology defenses to help reduce exposures
Chubb has released a new whitepaper, co-authored with Gordon Rees Scully Mansukhani LLP and PaymentWorks, that explores the common types of email social engineering schemes, particularly involving payments and suppliers, and how today’s cyber criminals are employing more sophisticated social engineering attacks than in the past. The paper, “Guarding Against Email Social Engineering Fraud: Re-examining a Global Problem,” also discusses ways in which companies can deploy technology and update their business practices to help verify information received electronically and authenticate the identity of business partners.
“With the heightened level of deception and manipulation involved in these attacks, email security requires a zero-trust approach,” said Christopher Arehart, Senior Vice President, Crime Product Manager, Chubb Financial Lines. “Therefore, it remains critical that businesses invest in updated technology defenses as well as adapt their processes and fundamentally change their procedures to fill the defense gaps that are weakened by compromised email.”
The FBI estimates that cyber criminals stole more than $28 billion through email fraud from 2016-2020, with an average loss per incident of more than $150,000.
According to the Chubb whitepaper, the most common social engineering fraud schemes include impersonation of executives, vendors and suppliers, exploitation of email accounts, and manipulation of vendor management accounts. Additionally, depending upon the type of scheme, the best ways to prevent these attacks include:
–Reconfiguring corporate email systems to better screen for spoofed emails and require Multi-Factor Authentication (MFA), to support more secure messaging from corporate email accounts;
–Reevaluating and rebuilding vendor management processes to account for changes to vendor data, rather than address them ad hoc during the payment process; and,
–Authenticating the information provided by using a modern technology platform that allows companies to onboard vendors or payees in a secure network environment to prove and verify identity.